Nutanix Flow Network Security with Citrix Virtual Apps and Desktops

This post will run through what Nutanix Flow Network Security is as well as steps that you could take to secure your Citrix Virtual Apps and Desktops environment using network segmentation.
- Overview
- Network Segmentation
- Nutanix Flow Network Security
- Implementing Nutanix Flow Network Security for Citrix Virtual Apps and Desktops
- Conclusion
Overview
Security is a big thing, always has been and always will be but when you tie security with a Citrix environment things get a little tougher. By nature, Citrix environments are typically an easy target for attackers, and they will try to get a foot hold in your environment and then spread out from there to the rest of your network. This is called Lateral Movement and is a common technique used my many attackers to get deeper and deeper into your world.
I have written about how to prevent lateral movement before, and you can read that here but what if you want to go a step further. Enter Network Segmentation.
What the hell is that you might ask, and why would I need to know about that in a Citrix Environment?
Wikipedia to the rescue, you can find a pretty decent starting point on network segmentation (NetSeg) here, so I would suggest reading that before you carry on with this post, so you have a basic understanding of what we are trying to achieve with this.
Network Segmentation
In essence, Network Segmentation does exactly what it says on the tin. You want to be able to split your network (or in this case your Citrix environment) into segments then define rules regarding the network traffic you want to allow in and out of that “segment” whilst blocking everything else.
Think about Citrix StoreFront as an example. You will want to allow port 443 into the servers from your defined user networks but not much else. The StoreFront servers will need to be able to talk to each other for subscription replication but outbound they may only want to be able to talk to the domain as an example. Now this is not an exhaustive list of the networking requirements but just an example to get the idea over.
What you want to be able to do is define all these rules so that you are only allowing the required traffic to move across your network and blocking everything else. This will stop attackers moving about your environment and taking advantage of a weak security posture.
This is easier said that done, I get that but implementing this will go a long way in making your platform more secure.
Citrix provides an exhaustive list of ports and protocols associated with all CVAD components. This document is regularly updated as component changes are implemented and is a good reference guide. Make sure that you map out your network requirements before starting out down this road as it will help reduce the chance of you pushing a policy that will break your environment.
Nutanix Flow Network Security
Since joining Nutanix as a Senior Solutions Architect I have been fortunate enough to get to play around with pretty much all the awesome technology that the engineers here come up with. One of these products is Nutanix Flow Network Security.
Here is the low down on what Flow Network Security is.
Flow Network Security delivers advanced networking and security services for AHV VMs, providing visibility into the virtual network, application-centric protection from network threats, and automation of common networking operations.
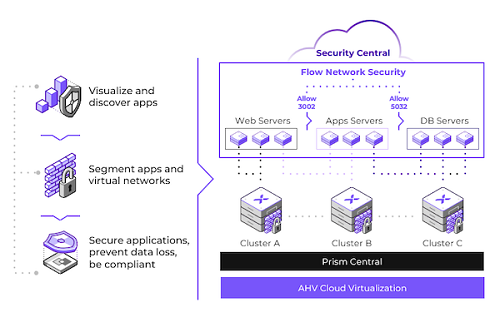
Fully integrated into AHV virtualization and the Nutanix Cloud Platform, Flow Network Security allows organizations to deploy software-defined virtual networking without installing additional products that have separate management and independent software maintenance requirements.
Flow Network Security provides application-centric policies that enable complete visibility and traffic control. This policy model allows administrators to implement fine-grained rules regarding traffic sources and destinations, or microsegmentation. These same policies make it possible to visualize traffic flowing within and between VMs. This granular level of control is an important part of a defense-in-depth strategy against modern datacenter threats.
Flow Network Security protects against new threats designed to spread laterally from one system to another in the same datacenter. Because perimeter-based firewalls traditionally only protect the environment from external threats, it can be difficult to repurpose them to protect internal traffic. Flow Network Security applies security rules between all applications and VMs in the datacenter, adding internal protection behind your perimeter firewall.
Implementing Nutanix Flow Network Security for Citrix Virtual Apps and Desktops
There is a great guide on the Nutanix documentation portal that will get you going with setting up Flow Network Security.
You can find the link to it here and the best thing is you can download it as a PDF and take it offline for some bedtime reading!!
Conclusion
Securing your Citrix Virtual Apps and Desktops environment is tough but by using products like Nutanix Flow Network Segmentation you can make things a little easier. I have found the configuration and implementation of the product really easy and intuitive and very good at improving your security posture right from the Prism Central interface.
Word of warning though, MAKE SURE YOU MAP THINGS OUT FIRST! Whilst implementing this I got bitten a few times by missing a port or protocol from the allow list so double-check your network diagram before applying the policies to ensure no downtime!
Thanks for reading.
